
OSI Model and TCP/IP Model Introduction
OSI Model and TCP/IP Model Introduction
The OSI model includes 7 layers. This model is definitely great for beginners, but it’s not all that best for modern communication. The information in the remaining columns will become clearer as I go through each layer. You can see the TCP/IP model (also called the DOD4 model).
The Application Layer – Layer 7
At the top of the OSI reference model sits layer 7, also called the “Application layer.” At this layer lies the interface of the applications we use every day. It is what we see on our screen. The applications we use, such as our Web browsers, don’t actually reside in the Application layer itself; however, they do interface with Application layer protocols, such as HTTP and other popular protocols, like Telnet, FTP, SNMP, HTTPS, DNS, DHCP, and so forth. There are a vast array of protocols working together at this layer.
These protocols are used to transmit information from a sending machine to a receiving machine. Using the same example as above, HTTP is a protocol used on the World Wide Web (WWW). It’s the Application layer protocol that defines the communication between a web browser and a web server. It specifically run on TCP port 80 by default and it’s how Internet users request HTML-formatted files.
The Presentation Layer -Layer 6
If you’ve ever seen a raw web page, you’ll understand that they are composed of HTML, JavaScript, ASCII/Unicode, image files, and audio files. These are things that the average Internet user cannot read. But, the Presentation layer converts this machine-readable code into something Internet users can easily read and “presents” it to the Application layer.
The Session Layer -Layer 5
As its name suggests, the Session layer is responsible for setting up, managing, and closing sessions between a client and server (e.g., Web browser and Web server). At any particular time, your computer can be managing hundreds of sessions simultaneously. Encryption can also occur at this layer; for instance, SSL/TLS encryption is initiated at the Session layer.
The Transport Layer -Layer 4
The Transport layer is a very important layer because this is where the well-known TCP and UDP protocols reside. These two protocols are responsible for end-to-end data transport and they also establish logical connections between a sending host and a destination host. But overall, the Transport layer’s primary responsibility is assembly and reassembly.
Let’s discuss how TCP works TCP creates a virtual circuit between the sending machine and the destination machine in order to initiate a reliable end-to-end data transport method. During the initial TCP Three-Way handshake, the sender and destination’s TCP stack agree on the amount of information in bytes that’s going to be sent before the recipient’s TCP sends back an acknowledgement (ACK). This fixed amount of bytes is called a “window,” and this mechanism helps pave the way towards reliable communication. TCP takes a data stream and separates it into small chunks called “segments.” Every segment is encapsulated with a TCP header and marked with a sequence number so that when the data stream is reassembled on the destination machine, it can be put back together in the correct order. The sequence numbers also help with resolving errors. For example, if the destination machine detects that it’s missing a segment in the data stream, it can request that specific segment by referring to the missing sequence number and requesting that the sending machine resend that segment. This certainly isn’t all TCP can do, but it does help paint a pretty picture of how reliable it can be when it relies on acknowledgements of data and retransmissions.
UDP is TCP’s little brother. It is not a reliable form of transport. But, if it’s not reliable, why use it? UDP just happens to be much faster than TCP because it is very simple! There is no three-way handshake, windows,
acknowledgements, or retransmissions of data This may make UDP unreliable and connectionless, but it does do a good job of transporting information that doesn’t require reliable delivery, such as video streaming. UDP does break down data streams into datagrams, but it’s not concerned with sequencing them or what order they arrive in.
Both TCP and UDP rely on port numbers to set up virtual circuits and communicate with the upper layers. Well-known TCP/IP applications, such as HTTP, FTP, Telnet, DHCP, and so forth, all have their own assigned port numbers. HTTP is TCP port 80; FTP is TCP ports 20 and 21, Telnet is TCP port 25, and DHCP is UDP ports 67 and 68. There are a total of 65,536 ports. Ports 0 through 1023 are the well-known ports. You don’t have to know them all, but you should know the port numbers of the well-known protocols.
The Network Layer -Layer -3
The Network layer is responsible for logical device addressing. At this layer an IP header is encapsulated to the information being transferred. When this happens, it is now called a “packet.” The IP header contains a source and destination IP address. These addresses are used by a layer 3 device (router) to “route” packets to the correct network where the destination machine resides.
IP, ICMP, and ARP work at this layer. IP is pretty much responsible for logical addressing. ICMP, or Internet Control Message Protocol, is used for management and troubleshooting. Popular ICMP utilities include ping and traceroute. And ARP, or Address Resolution Protocol, is used to find MAC addresses on the LAN.
The Data Link Layer -Layer 2
At the Data Link layer, packets are encapsulated with a custom header, either 802.3 (Ethernet) or 802.11 (wireless). This header contains the sender’s MAC address and the destination MAC address. Messages at the Data Link layer are called “frames“.
The primary responsibility of the Data Link layer is to ensure that messages are delivered to the correct device on the LAN using these MAC addresses. Layer 2 devices (Switches) work at this layer. They send frames out to destination machines or receive frames from sending machines. The Data Link layer is split into two sub-layers:
The Logical Link Layer (LLC)
The LLC is responsible for error-checking, frame synchronization, error control, flow control, and encapsulation. Think of it as the brain of the Data Link layer that knows what to do with frames as they arrive.
The MAC Address layer
This sub layer is concerned with how the information will be placed on the physical medium (e.g., the wire, fiber-optic, radio waves, etc.). MAC addresses are 48-bits long and they are represented in hexadecimal characters, for example, XX-XX-XX-XX-XX-XX. Every hexadecimal character (X) is equivalent to 4-bits. The first 24 bits are called the Organizationally Unique Identifier (OUI), but is now commonly called the Extended Unique Identifier (EUI). This identifies the manufacturer. The last 24 remaining bits are the device ID. Theoretically, MAC addresses should be unique, but this isn’t always true.
The Physical Layer -Layer 1
And finally, the Physical layer is the communication media that sends and receives “bits.” When a message is put on the wire, the bits are represented in either a 1 or 0. But, different communication media represent these values in different ways. A hub would be considered a layer 1 device because it simply forwards all information out to every port. NICs, on the other hand, are both a layer 1 and layer 2 device. However, most people would argue that they are layer 2 only.
OSI model Layer 1 attacks
Layer 1 refers to the physical aspect of networking – in other words, the cabling and infrastructure used for networks to communicate. Layer 1 attacks focus on disrupting this service in any manner possible, primarily resulting in Denial of Service (DoS) attacks. This disruption could be caused by physically cutting cable right through to disrupting wireless signals.
OSI model Layer 2 attacks
Layer 2 of the OSI model is the data link layer and focuses on the methods for delivering data blocks. Normally, this consists of switches utilising protocols such as the Spanning Tree Protocol (STP) and the Dynamic Host Configuration Protocol (DHCP), which is used throughout networking for dynamic IP assignment.
Attacks at this layer can focus on the insecurity of the protocols used or the lack of hardening on the routing devices themselves. As switches focus is on providing LAN connectivity, the majority of threats come from inside the organisation itself. Layer 2 attacks may also include MAC flooding or ARP poisoning.
OSI model Layer 3 attacks
Layer 3 is the network layer and utilises multiple common protocols to perform routing on the network. Protocols consist of the Internet Protocol (IP), packet sniffing and DoS attacks such as Ping floods and ICMP attacks. Because of their layer 3 nature, these types of attacks can be performed remotely over the Internet while layer 2 attacks primarily come from the internal LAN.
OSI model Layer 4 attacks
Layer 4 is the transport layer and utilises common transport protocols to enable network communications. This may include the Transport Control Protocol (TCP) and Universal Data Protocol (UDP).
Port scanning, a method by which to identify vulnerable or open network ports, operates at layer 4 of the OSI model. Implementing effective firewalls and locking down ports only to those required can mitigate risks at this level.
OSI model layer 5-7
Above layer 4, we are looking primarily at application level attacks which result from poor coding practices. Vulnerabilities in applications can be exploited through attacks such as SQL injection, where the developer has failed to ensure that user input is validated against a defined schema.
The attacker would then input code to extract data from the database (e.g. SELECT * from USERS). As the application fails to validate this input, the command is run and data extracted. To reduce this risk, developers must ensure that best practice development guides are adhered to.
TCP/IP Model Introduction
What is the TCP/IP Model?
TCP/IP Model helps you to determine how a specific computer should be connected to the internet and how data should be transmitted between them. It helps you to create a virtual network when multiple computer networks are connected together. The purpose of TCP/IP model is to allow communication over large distances.
TCP Characteristics
Here, are the essential characteristics of TCP/IP protocol
- Support for a flexible TCP/IP architecture
- Adding more system to a network is easy.
- In TCP/IP, the network remains intact until the source, and destination machines were functioning properly.
- TCP is a connection-oriented protocol.
- TCP offers reliability and ensures that data which arrives out of sequence should put back into order.
- TCP allows you to implement flow control, so sender never overpowers a receiver with data.
Four Layers of TCP/IP model
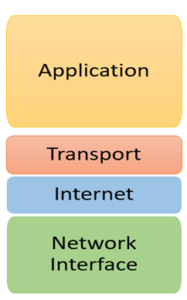
The functionality of the TCP IP model is divided into four layers, and each includes specific protocols.
TCP/IP is a layered server architecture system in which each layer is defined according to a specific function to perform. All these four TCP/IP layers work collaboratively to transmit the data from one layer to another.
- Application Layer
- Transport Layer
- Internet Layer
- Network Interface
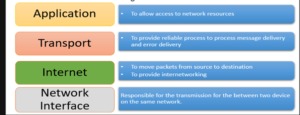
Application Layer
Application layer interacts with an application program, which is the highest level of OSI model. The application layer is the OSI layer, which is closest to the end-user. It means the OSI application layer allows users to interact with other software application.
Application layer interacts with software applications to implement a communicating component. The interpretation of data by the application program is always outside the scope of the OSI model.
Example of the application layer is an application such as file transfer, email, remote login, etc.
The function of the Application Layers are:
- Application-layer helps you to identify communication partners, determining resource availability, and synchronizing communication.
- It allows users to log on to a remote host
- This layer provides various e-mail services
- This application offers distributed database sources and access for global information about various objects and services.
Transport Layer
Transport layer builds on the network layer in order to provide data transport from a process on a source system machine to a process on a destination system. It is hosted using single or multiple networks, and also maintains the quality of service functions.
Important functions of Transport Layers:
- It divides the message received from the session layer into segments and numbers them to make a sequence.
- Transport layer makes sure that the message is delivered to the correct process on the destination machine.
- It also makes sure that the entire message arrives without any error else it should be retransmitted.
Internet Layer
An internet layer is a second layer of TCP/IP layers of the TCP/IP model. It is also known as a network layer. The main work of this layer is to send the packets from any network, and any computer still they reach the destination irrespective of the route they take.
The Internet layer offers the functional and procedural method for transferring variable length data sequences from one node to another with the help of various networks.
Message delivery at the network layer does not give any guaranteed to be reliable network layer protocol.
Layer-management protocols that belong to the network layer are:
- Routing protocols
- Multicast group management
- Network-layer address assignment
The Network Interface Layer
Network Interface Layer is this layer of the four-layer TCP/IP model. This layer is also called a network access layer. It helps you to defines details of how data should be sent using the network.
It also includes how bits should optically be signaled by hardware devices which directly interfaces with a network medium, like coaxial, optical, coaxial, fiber, or twisted-pair cables.
Differences between the OSI and TCP/IP model:
| OSI Model | TCP/IP model |
| It is developed by ISO (International Standard Organization) | It is developed by ARPANET (Advanced Research Project Agency Network). |
| OSI model provides a clear distinction between interfaces, services, and protocols. | TCP/IP doesn’t have any clear distinguishing points between services, interfaces, and protocols. |
| OSI refers to Open Systems Interconnection. | TCP refers to Transmission Control Protocol. |
| OSI uses the network layer to define routing standards and protocols. | TCP/IP uses only the Internet layer. |
| OSI follows a vertical approach. | TCP/IP follows a horizontal approach. |
| OSI model use two separate layers physical and data link to define the functionality of the bottom layers. | TCP/IP uses only one layer (link). |
| OSI layers have seven layers. | TCP/IP has four layers. |
| OSI model, the transport layer is only connection-oriented. | A layer of the TCP/IP model is both connection-oriented and connectionless. |
| In the OSI model, the data link layer and physical are separate layers. | In TCP, physical and data link are both combined as a single host-to-network layer. |
| Session and presentation layers are not a part of the TCP model. | There is no session and presentation layer in TCP model. |
| It is defined after the advent of the Internet. | It is defined before the advent of the internet. |
| The minimum size of the OSI header is 5 bytes. | Minimum header size is 20 bytes. |
Advantages of the TCP/IP model
Here, are pros/benefits of using the TCP/IP model:
- It helps you to establish/set up a connection between different types of computers.
- It operates independently of the operating system.
- It supports many routing-protocols.
- It enables the internetworking between the organizations.
- TCP/IP model has a highly scalable client-server architecture.
- It can be operated independently.
- Supports a number of routing protocols.
- It can be used to establish a connection between two computers.
TCP/IP Model Attacks
| TCP/IP model | Protocols | Attack |
| Application | FTP, HTTP, Telnet, DNS, SNMP | Application attacks, exploit code, malicious software e.g. Trojans, Buffer overflowProtocol attack, NetBIOS enumeration, clear text extractionSYN attacks, password attack, Session hijacking |
| Transport | TCP, UDP | DOS attacks, service enumeration, flag manipulation, port scanning, IP spoofing |
| Network (Internet) | IP, ICMP, IGMP, ARP | Routing attacks, ARP poisoning, IP attacks, MAC flooding, ICMP assault such as Smurf |
| Data Link (Network Access) | Ethernet, Token Ring, Other Link-Layer Protocols | MAC spoofing, WEP cracking, passive and active sniffingLock picking, physical access attack, hardware hacking, wiretapping and interception |
References:
https://www.giac.org/paper/gsec/2868/osi-defense-in-depth-increase-application-security/104841
https://us-cert.cisa.gov/sites/default/files/publications/DDoS%20Quick%20Guide.pdf
https://www.utc.edu/center-academic-excellence-cyber-defense/pdfs/course-paper-5620-attacktcpip.pdf
